2026年度继续教育学时
0/42
专业课
0/30
公需课
0/18
选修课
| 序号 | 名称 | 类别 | 学时 | 状态 | 开始时间 | 结束时间 |
| 8 | 2025年雷州市中小学(幼儿园特殊教育学校)教师师德修养及科学素养专题研修 | 专业/选修课 | 36+18 | ✅已完成 | 2025-11-18 00:00:00 | 2025-12-23 23:59:59 |
| 7 | 2025年暑假教师研修(9月15日起领取证书) | 专业课 | 10 | ✅已完成 | 2025-07-20 00:00:00 | 2025-09-30 23:59:59 |
| 6 | 广东省教育技术论文写作培训 | 专业课 | 6 | ✅已完成 | 2025-07-04 00:00:00 | 2025-10-10 23:59:59 |
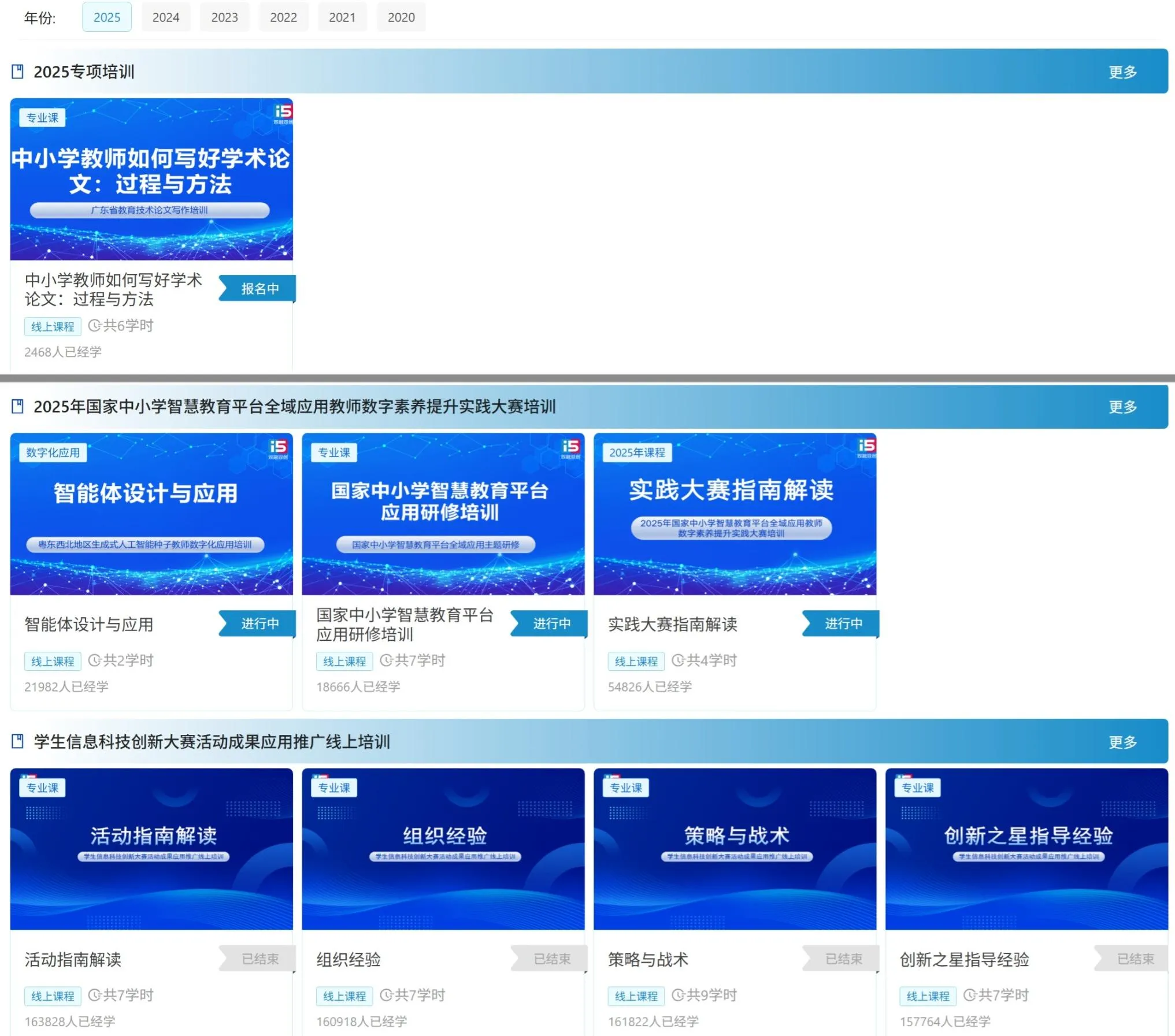
| 5 | 2025年国家中小学智慧教育平台全域应用教师数字素养提升实践大赛培训 | 专业课 | 13 | ✅已完成 | 2025-03-14 00:00:00 | 2025-08-31 23:59:59 |
| 4 | 学生信息科技创新大赛活动成果应用推广线上培训 | 专业课 | 30 | ✅已完成 | 2025-01-10 00:00:00 | 2025-05-31 23:59:59 |
| 3 | 国家中小学智慧教育平台应用专项培训 | 专业课 | 24 | ✅已完成 | 2025-05-09 00:00:00 | 2025-06-30 23:59:59 |
| 2 | 2025年寒假教师研修(3月17日起领取证书) | 专业课 | 6 | ✅已完成 | 2025-01-25 00:00:00 | 2025-03-31 23:59:59 |
| 1 | 新质生产力与现代化产业体系 | 公需课 | 30 | ✅已完成 | 2025-05-14 00:00:00 | 2026-04-30 23:59:59 |
 6️⃣2025年雷州市中小学(幼儿园特殊教育学校)教师师德修养及科学素养专题研修✅
2025年11月18日 开始 - 2025年12月23日 截止
6️⃣2025年雷州市中小学(幼儿园特殊教育学校)教师师德修养及科学素养专题研修✅
2025年11月18日 开始 - 2025年12月23日 截止
一、研修对象
全市未完成 2025 年专业课 42 学时、选修课 18 学时的中小学(幼儿园、特殊教育学校)在职在岗教师
二、研修学时
根据本年度已开展寒假研修、暑期研修(共计16专业课学时)的实际情况,本次研修学时为 54 学时(含 36 专业课学时+18选修课学时)。由雷州市教师发展中心将按要求完成学习任务的合格学员学时录入“广东省中小学教师继续教育信息管理平台”。
三、课程设置
本次网络研修课程分为专业课程和选修课程,选修课对应“师德修养”模块,专业课对应“科学素养”模块。“师德修养”模块有 2 个课程,共计 18 个选修学时,其中课程 1《大力弘扬教育家精神》16 个学时,课程 2《教育惩戒规则的理解与适用》2 个学时。“专业素养”模块有 1 个课程(课程 3《科学素养提升》),共计 36 个专业学时。
四、研修方式
研修采用网络学习形式进行。
五、研修时间
2025年11月18日-12月23日
六、研修平台
国家中小学智慧教育平台(https://basic.smartedu.cn/)
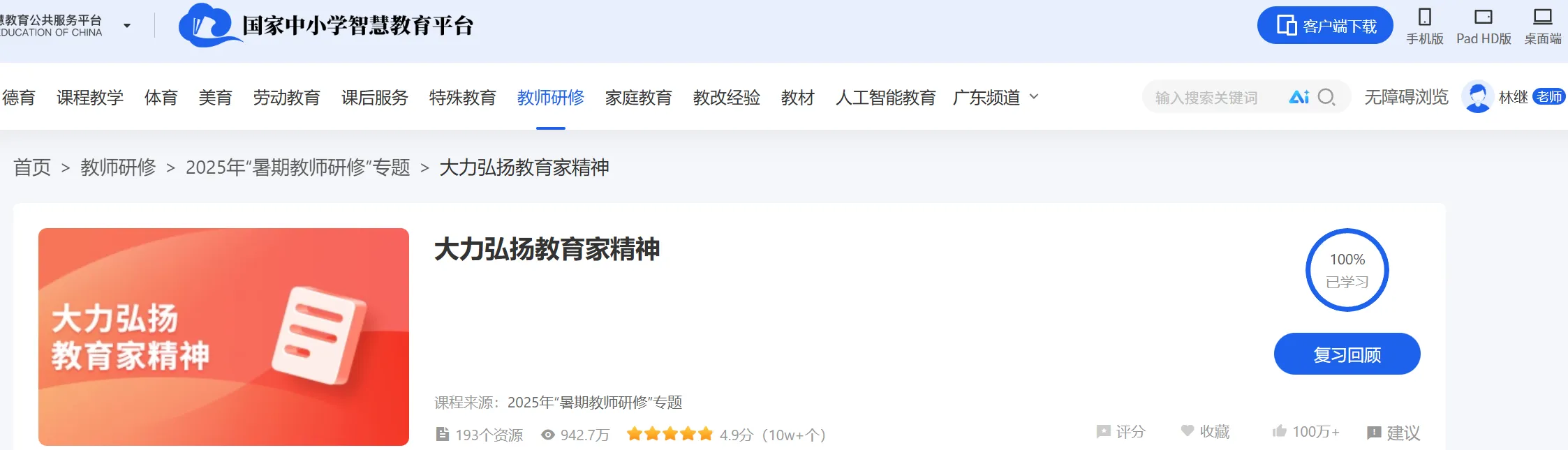
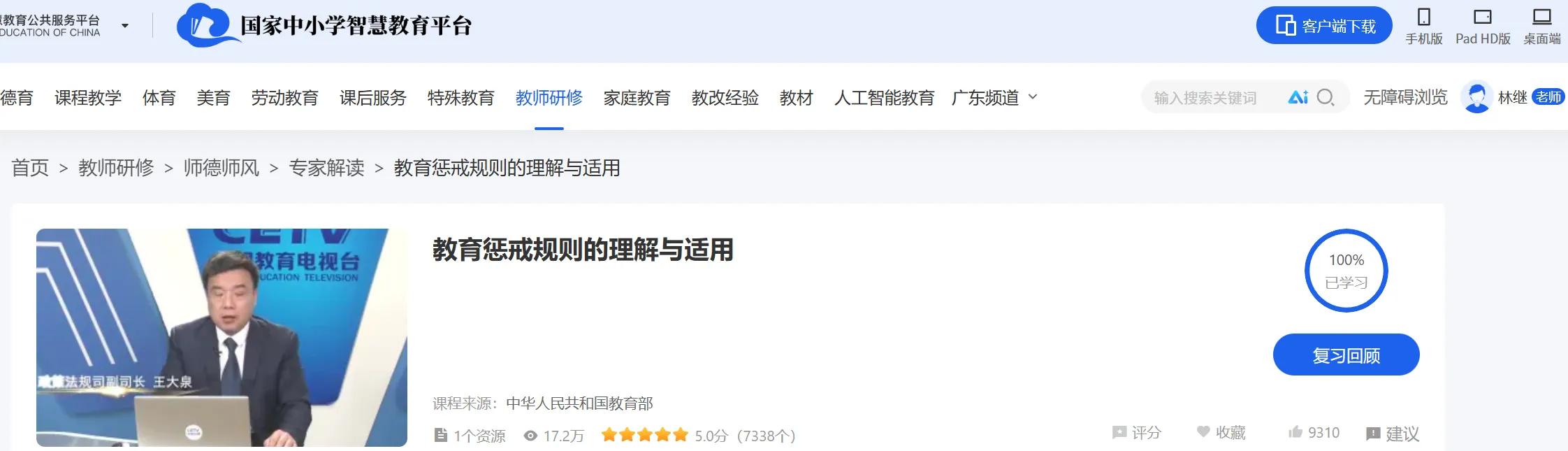
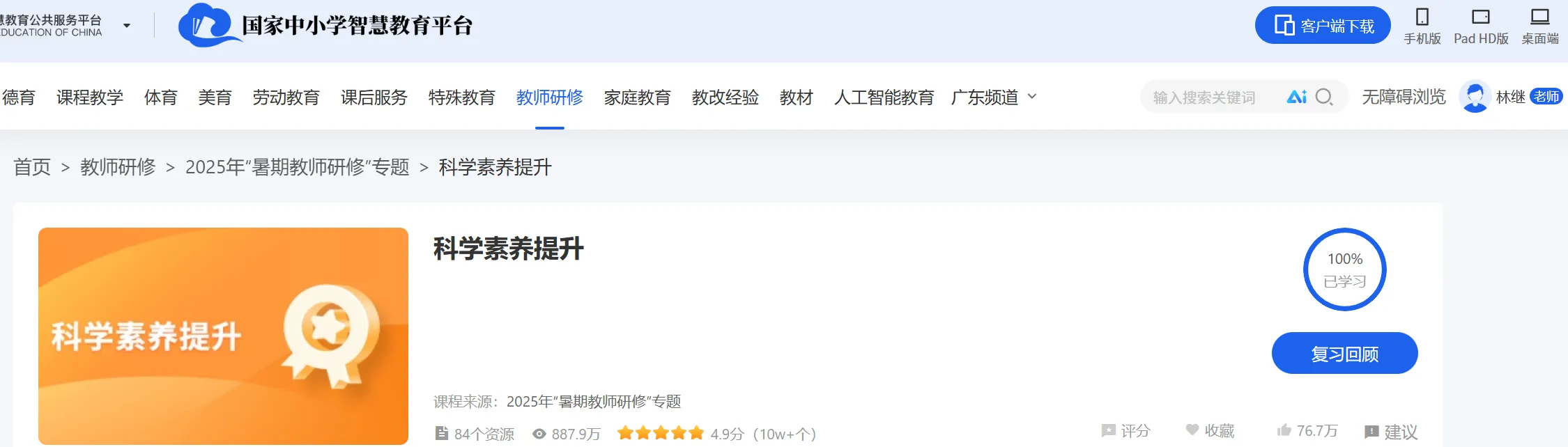
5️⃣2025年广东公需课答案(公需课30学时)✅ 2025年5月14日 开始 - 2026年4月30日 截止
学习途径 (更新于 2021.06.25 21:00)
广东省教师继续教育信息管理平台: https://jsglpt.gds.edu.cn/咨询电话:400-998-9352 ( 帐号与密码说明 | 客服 | 留言)
考核答案
新质生产力与现代化产业体系
B, D, A, D, A, B, B, A, B, A,ABC, ABCD, ABCDE, ABC, ACD,
ABC, ABC, ABC, ABD, ABDE,
A, A, A, A, B, B, B, A, A, B
人工智能赋能制造业高质量发展
C, D, B, B, B, B, C, B, C, B,ABC, ABCD, ABD, ABC, ABCD,
ABC, AB, ACD, ABC, ABCD,
A, A, B, B, B, B, A, A, A, A
学习结果
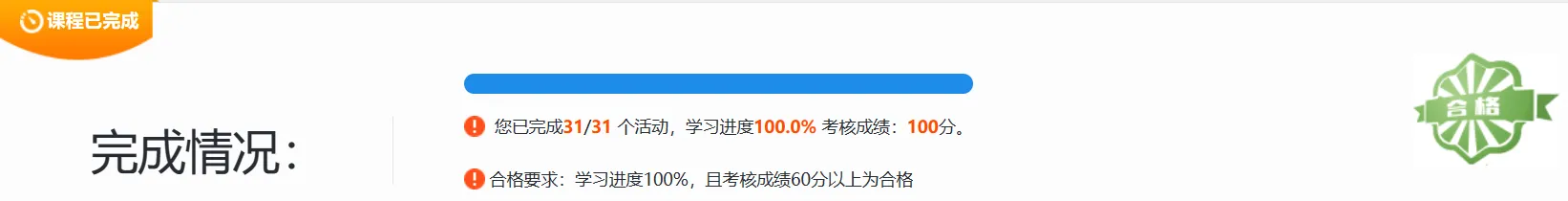


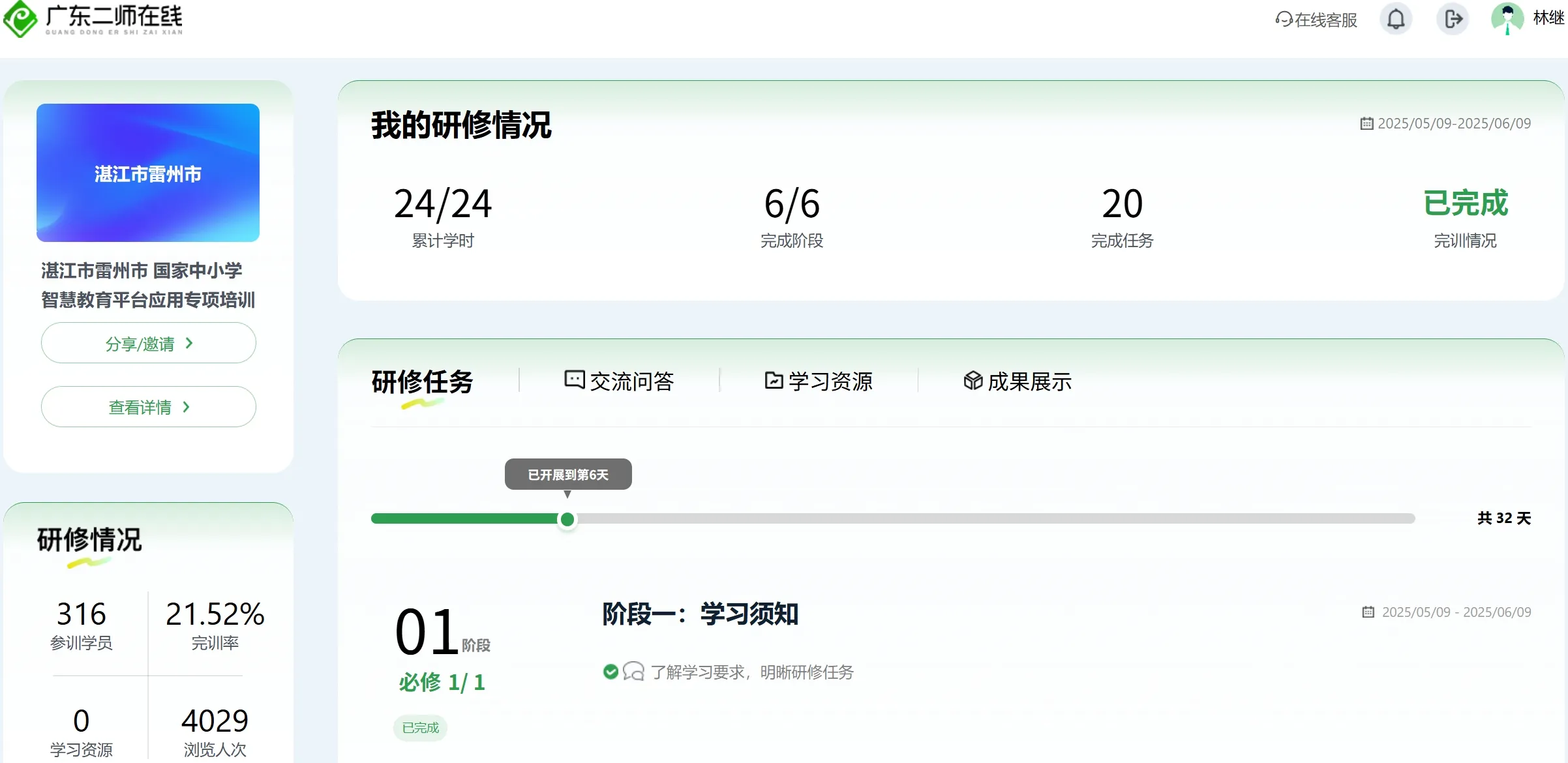
 4️⃣智慧教育平台应用专项培训(专业课24学时)✅
研修时间: 2025年05月09日-2025年06月09日
4️⃣智慧教育平台应用专项培训(专业课24学时)✅
研修时间: 2025年05月09日-2025年06月09日
【广东第二师范学院】老师您好,您已报名国家中小学智慧教育平台应用专项培训,培训时间为2025年5月9日 - 6月9日,请登录广东二师在线平台进入专项工作坊学习(网址: https://online.gdei.edu.cn )。登录账号为身份证件号,初始密码:peixun20250509@Gd,注意G要大写。如需了解培训详情,请点击以下链接查看培训通知: https://www.wjx.cn/vm/rauniXB.aspx# 。登录平台若显示单位不正确,请耐心等待数据更新。如有疑问,可拨打服务热线 400-998-9352 咨询。祝您培训顺利!
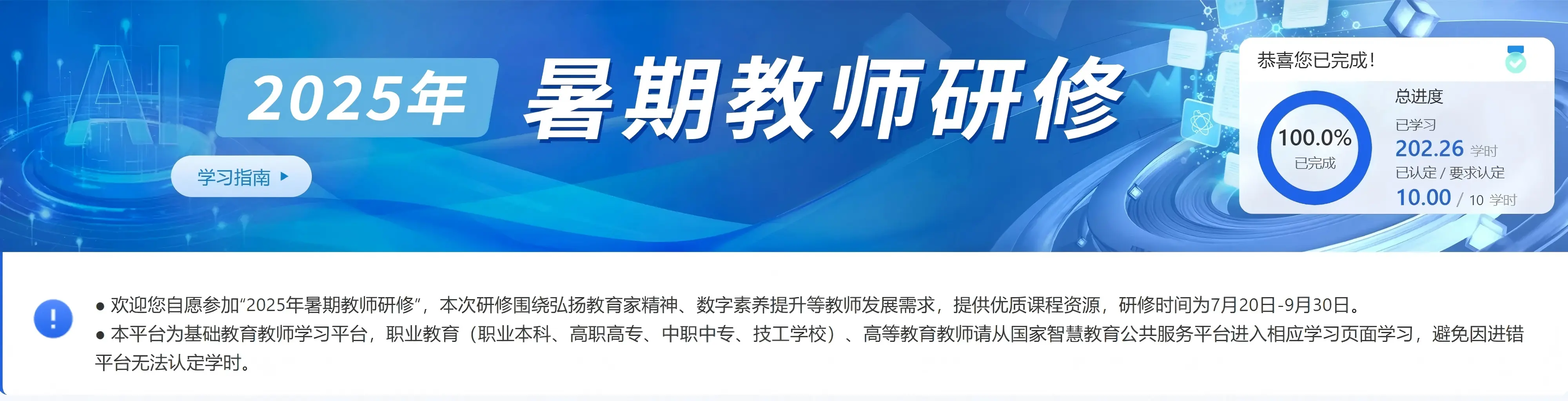
 3️⃣2025年暑假教师研修(专业课10学时)✅
2025年7月20日 开始 - 2025年9月30日 截止
3️⃣2025年暑假教师研修(专业课10学时)✅
2025年7月20日 开始 - 2025年9月30日 截止
【2025年暑期研修提醒】更新于2025.7.21 22:50
暑期研修常态化,研修时间为7月20日-9月30日。
请通知老师们进入相应学段的学习页面学习,避免因进错平台无法认定学时。完成本次研修,平台为教师认定10学时。
基础教育教师学习平台:https://basic.smartedu.cn/training/2025sqpx
职业教育教师学习平台:https://teacher.vocational.smartedu.cn/h/subject/summer2025/
智慧平台客服电话:4001910910(工作日 8:30-17:00)
省时省事的学习内容: 每个单元学习前10个足够了。 (或)第一个9个,第二个7个,第三个2个,第四个5个, 下边三课时那个大模块里边有四个分类,我弄的第三个里边,弄了7个。
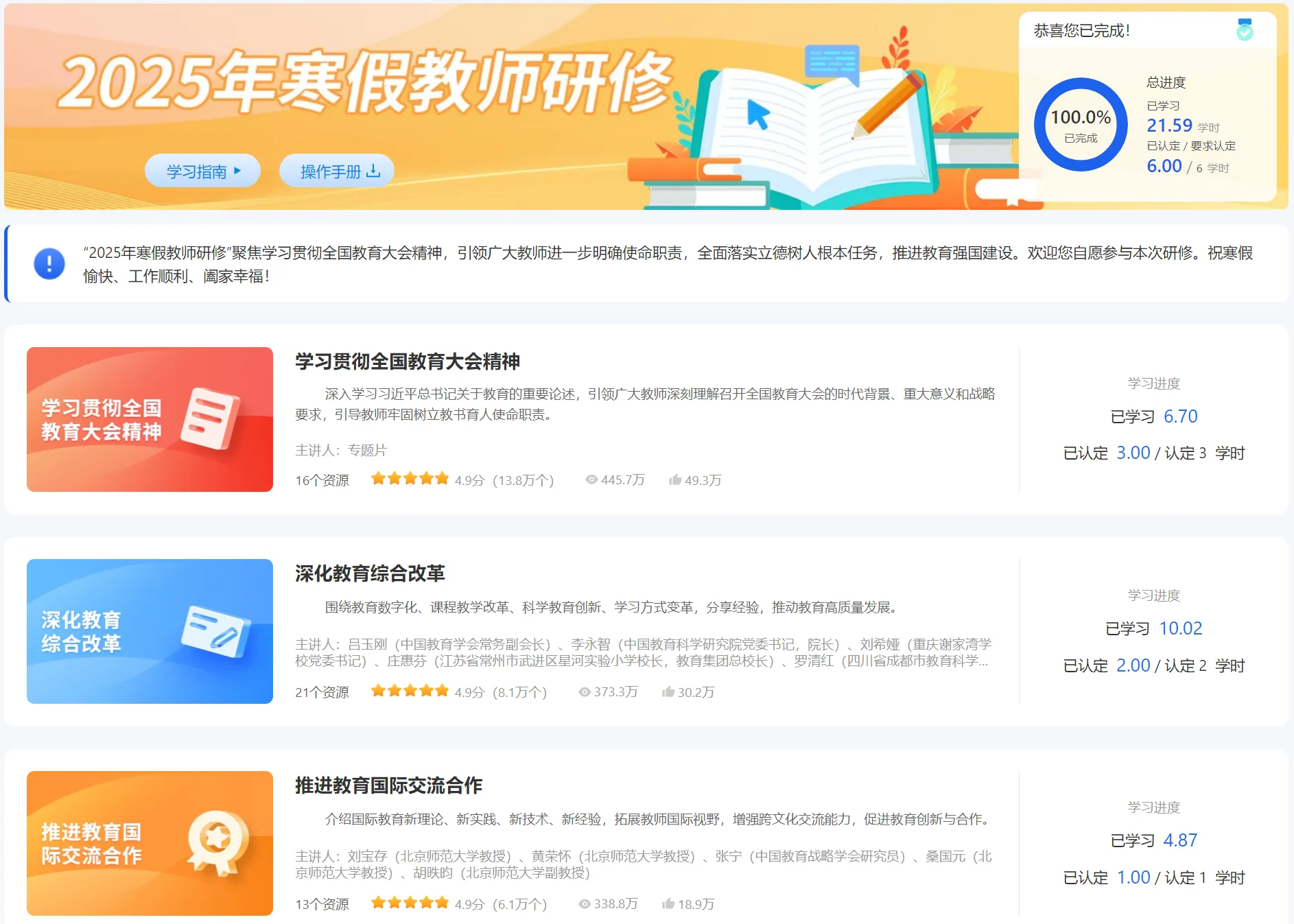
2️⃣2025年寒假教师研修(专业课6学时)✅ 2025年1月25日 开始 - 2025年3月31日 截止
省时省事的学习内容: 第一单元学习前五个;第二单元学习前四个; 第三单元学习第一小节第一个; 第三单元学习第二小节第二个。
 1️⃣广东省教育双融双创智慧共享社区(专业课49学时)✅
线上培训课程
1️⃣广东省教育双融双创智慧共享社区(专业课49学时)✅
线上培训课程
①平台没有单位,可申请新增: https://srsc.gdedu.gov.cn/pub/srsc/addUnit
②单位更名:可申请变更: https://srsc.gdedu.gov.cn/pub/srsc/editUnit
③两个单位合并申请: https://srsc.gdedu.gov.cn/pub/srsc/mergeUnit
在双融双创修正完,再去继教网个人信息上核对一遍,两个平台之间姓名、身份证一致就能正常导入。
 💠网课代挂说明
💠网课代挂说明1、我这边都是通过真实浏览器进行网课代挂,一般都是 1 倍速进行播放(特殊要求除外)。可以保证学习记录不异常,学时正常记录。
2、我崇尚的理念是:一次合作,终身合作。有代挂需求的人基本上都是体系内的公职人员,年年都要学网课,最害怕学习出现问题(如倍速/秒过后学时异常被通报批评,无法获取本年度学分等),我这边都是真实浏览器代挂,不倍速,不秒过,积累老客户,做回头客生意。
3、收费标准:每位20元。
4、需要帮忙的老师可以在赞赏码留言栏填写帐号与密码。

继续教育 2020-04-18 20:10:24 通过 网页 浏览(7681084) 打印
共有10条评论!
谢谢您的答案!
谢谢您的答案,辛苦了!
谢谢您的答案,辛苦了!
专业课和选修课在德诚选择吗?
林继回复:在德诚平台可以报名学习专业课和选修课。只是第一批学习已经在4月底终止,不知道第二批什么时候开始报名学习。
谢谢亲贡献的答案
感谢您的答案!
谢谢你的答案
谢谢你的答案
谢谢你的答案
谢谢您的答案